Today’s modern IT infrastructure has enabled us to work freely outside our offices and network perimeter. We routinely use our endpoint devices to access corporate email, SaaS apps, and download documents. Remote and mobile computing has boosted our productivity, but how safe is it when research says 70 percent of successful breaches start on the endpoint?
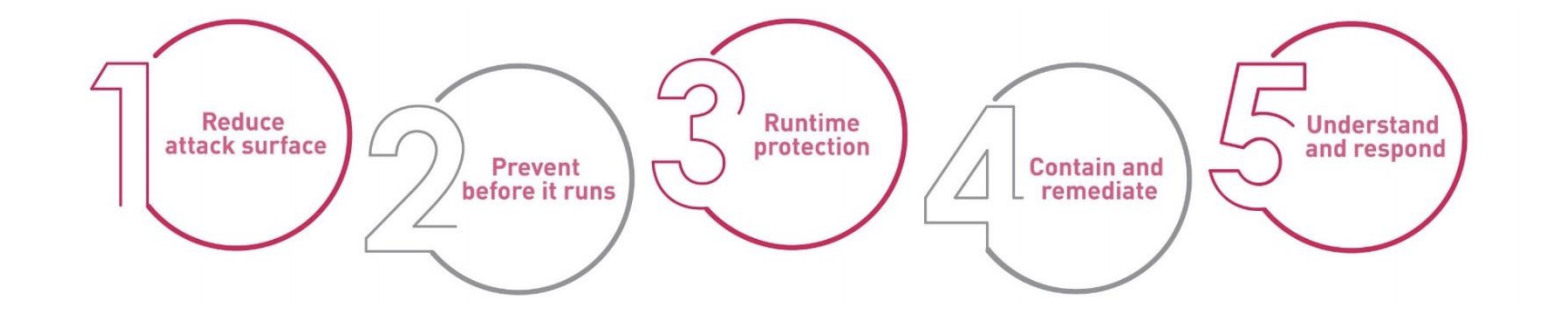
Read our whitepaper on the 5 best practices to elevate endpoint security.
66 percent of respondents say their organization will experience a data breach or cybersecurity exploit that will seriously diminish shareholder value.