The business landscape has changed dramatically in the last two years, especially from an IT perspective. Managing IT in the modern era requires overseeing remote users, hybrid users, and a wide range of devices and endpoints. How do you secure it all? That’s the topic of this presentation.
Zones President and Chief Operating Officer Derrek Hallock kicks off the presentation with an opening keynote on the topic. Next, Andrew Reese, Cybersecurity Practice Head at Zones, leads a panel discussion that goes in-depth on the inherent challenges of cybersecurity today.
Watch the video above. You’ll also find a transcript of the panel discussion after the speaker bios below.

Speaker: Derrek Hallock
Position: President & Chief Operating Officer, Zones
Background: Derrek Hallock was named President in 2020 in addition to holding the Chief Operating Officer role at Zones since 2017. In this role, Hallock leads the company's Partner and Product Management (PPM), Marketing, Operations, and Supply Chain, along with Logistics, Integration, Technology Solution Centers, and Service Delivery divisions. In this role, he is responsible for driving innovation and collaboration across the company's partner ecosystem, increasing operational and supply chain efficiency, optimizing costs, elevating the Zones brand, and strengthening global service delivery for Zones clients, with an overarching mission of enabling industry-leading customer experiences and client satisfaction.
Hallock leverages broad industry experience gained at SED International, Tech Data, and CompuCom Systems, where he led a progression of sales management, strategic marketing, and global supply chain organizations. He graduated from Michigan State University with a degree in Supply Chain Management and went on to earn his Executive Master of Business Administration from the University of Washington Foster School of Business.

Speaker: Andrew Reese
Position: Practice Head, Cyber Security, Zones Cybersecurity & Services
Background: Security and Compliance Subject Matter Expert: Extensive hands-on experience measuring, assessing, designing, implementing, improving, and managing Information Security Management Systems (ISMS) and cybersecurity programs. Well versed in aligning organizational controls with legal, regulatory, and contractual requirements, as well as, business goals and objectives. Consulting experience working with hundreds of organizations, of all sizes and across major vertical markets, using well-documented industry best practices and methodologies.

Speaker: Scott Foote
Position: CISO, DPO, Managing Director, Phenomenati Consulting
Background: Bringing "order to chaos" drives every role Scott has played. First as an engineer, then product executive, then analyst, board member, and most recently as a CISO. Scott is an experienced cybersecurity executive, designing security and privacy into digital transformation initiatives for his clients. With more than 30 years of technology leadership experience in cybersecurity and the broader software industry, Scott has an acute ability to understand and map organizational needs to security models, architectures, solutions, and technologies. His primary area of expertise has been information security since the late 1980s; however, Scott’s technical experience ranges from operating system kernel technologies, to the gamut of filesystem / database and info storage, to network engineering, to packaged commercial applications such as SCADA, B2B and CRM solutions; from on-premise to cloud deployments.

Speaker: Joel Jacobs
Position: Ex-MITRE CIO, CSO, Advisor & Consultant, Phenomenati Consulting
Background: Joel is an accomplished Chief Information Officer and Chief Security Officer with a demonstrated history of success in information technology and corporate operations. He is skilled in Strategy, Operations, Service Management, Professional Services Leadership, and Cyber Security. Joel is a regular public speaker and leader in technology and CIO forums.
Edited for context as needed
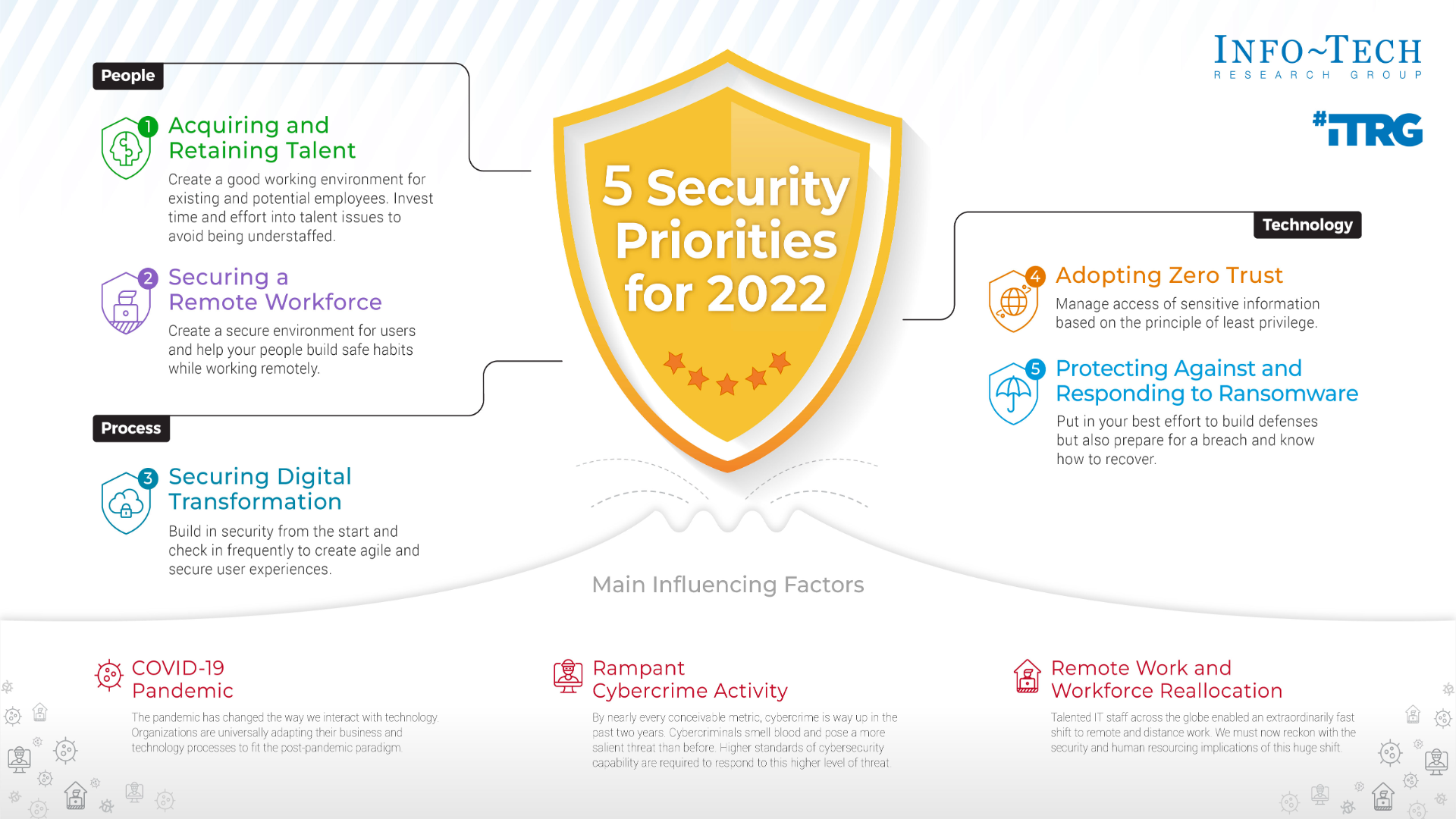
Andrew Reese: I want to take the panelists through the list of 2022’s top five security priorities, as identified by Info-Tech Research Group in their report, Security Priorities 2022: Securing the Workforce in the Remote Environment.
Let’s start with security priority number five and work our way up to number one.
Andrew: Ransomware attacks have transformed in 2021 and show absolutely no signs of slowing down in 2022. There is a new major security breach every week, despite organizations spending over $150 billion in a year on cybersecurity. (Nasdaq, 2021)
And now ransomware as a service (RaaS) is commonplace, and attackers are doubling down by holding encrypted data ransom and also demanding payment under threat of disclosure for the data that they have exfiltrated. And they’re actually making good on their threats.
Our Info-Tech Research Group business partner] talked about five recommendations. One of those is to be prepared for a breach. Because there is no guarantee that an organization will not fall victim to ransomware. So instead of putting all their effort into prevention, perhaps organizations should also put effort into planning and responding to a breach.
What additional steps do you think should be added to prepare for a breach, Joel?
Joel Jacobs: The first thing is to make sure that you understand the status of your backups and whether you have immutable storage. We’re seeing in our clientele real concerns about making sure that their backups are workable and that they’ve been tested regularly. Insurance companies are beginning to insist on this.
The other part is making sure to decide how you’re going to decide how to handle it. That means ensuring that you have an incident response plan that is tuned to ransomware. Ransomware attacks were up 82% from 2020 to 2021, and as you say, there’s no sign of it letting up.
Andrew: The next recommendation from Info-Tech is security awareness training and phishing detection. You know, phishing continues to be the main point of entry of ransomware. Investing in an awareness and detection program among your end users may be the most impactful countermeasure that you can put in place.
What are some of the techniques you would use to properly configure your “Human Firewall,” Scott?
Scott Foote: It’s interesting you bring this one up because I usually talk about patching the humans, right – vulnerabilities and the patching of the human – and that’s what security awareness training does. And one of the biggest things we need to recognize is that humans are inherently helpful and they’re inherently trustful. So, we’ll talk about zero trust on the technology side later, but we endeavor to get humans to have zero trust in their interactions. Be polite. Be engaging. But don’t immediately trust.
You will be phished socially, whether it’s on email, social media or even live via the phone. Train them to be sensitive to the fact that there are people trying to exploit their inherent trust.
Joel also talks about training in terms of snackable bites. We see a lot of vendors as we do assessments for the programs and the clients we work with, and we try to encourage them not to just queue up three hours’ worth of security training at the end of the year, but [rather] to make it consumable in much smaller pieces and spread it out across the entire year. [You’ll get] much better engagement with the workforce.
Andrew: Those are all very good points. [Info-Tech also recommends] encrypting and backing up our data – encrypt our data so even if there is a data breach the attackers won’t have a copy of your data. And also, keep regular backups of the data and put it in a separate location so that you’ll still have the data to work on after a breach occurs.
What are some keys points a client should consider when looking at encryption and data backup solutions?
Joel: Make sure you’re testing. Make sure you’ve got geographic distribution traffic separation as well. Making sure that your backups are restorable is the number one key. If you’re able to encrypt and put multifactor authentication in front of your backup environment that’s a big step forward, as well.
Scott: Yes, part of that testing should be to make sure that you can recover from the data within your objectives – your RTO and your RPO. Your recovery time objective, meaning what’s the window; and the recovery point objective, meaning how much data can you afford to lose. It isn’t sufficient to say, “I can get the backups back.” Make sure you can meet those objectives.
Andrew: They talk about zero trust adoption, as well: Always verify at every step of interaction, even when access is requested by internal users, and that you manage access of sensitive information based on the principle of least privilege . . . which brings us to our fourth security priority…
Andrew: The top reasons for building a Zero Trust Program:
Those are just some of the things. They talk about starting small. Don’t put all your eggs in one basket by deploying zero trust in a wide swath. Rather, start as small as possible to allow for growing pains without creating business friction – or sinking your project altogether.
Where do you think is a good place to start small?
Scott: I would say look at network segmentation. We don’t have to start with core business systems and dismantle them into microservices and put gateways, right? That’s the vision of zero trust longer term. But in the near term, we can do network segmentation of the environment.
Very typically we’ll see people that have rolled out IoT devices. It could be conference room equipment, the video screens that are in the break rooms, the HVAC components . . . but they don’t have a separate IoT network. All of that equipment is on the exact same network as the general user traffic.
This idea of network segmentation is fairly straightforward to do, especially in today’s world where we’re using Wi-Fi rather than a [network] cable. And understand that you want to isolate traffic based upon the types of information that traffic needs to have access to – always looking at isolating traffic that has the least privilege on its own networks.
Andrew: They also recommend being aware of “too-good-to-be-true” products. Zero trust is a powerful buzzword. A lot of people are using it and vendors know it. You have to be skeptical and do your due diligence to make sure your new security partners in zero trust are delivering what you need.
Going back to you, Joel, what kinds of due diligence would you recommend?
Joel: The overpromising isn’t unique to zero trust. We’ve had overpromising vendors for forever . . . and especially in security where they’ve got the one thing that will complete your defenses and reassure your environment.
Zero trust has become the next big thing, the next shiny object. But I think making sure that you’re starting with real criteria about what you’re trying to achieve – define it from the start. And press for reference implementations. Reference accounts that the vendors and consultants have put in place already. See if they have been able to live up to their promises because there’s a lot of overpromising.
Andrew: Yes, so basically you need to build a sensible road map of where you are and where you need to get to.
Zero trust principles can be applied in a number of different ways, so you need to find out where you need to start. Between identities, devices, networking, and data, decide on a use case that will be your pilot project and then refine your approach.
Andrew: Digital transformation is occurring at an ever-increasing rate these days. As Microsoft CEO Satya Nadella said early in the pandemic, “We’ve seen two years’ worth of digital transformation in two months.”
We’ve heard similar stories from Info-Tech members who deployed rollouts that were scheduled to take months that happen basically over a weekend.
Engaging the business early and often is kind of like a requirement. Despite the risks, organizations engage in digital transformations because they also have huge business value. So, security leaders should not be seeking to slow or stop digital transformations; [instead] they should be engaging the business early and then trying to get ahead of the risk to enable a successful transformation.
What are some good ways to engage stakeholders?
Scott: This is an important place to start with those stakeholders. We talk a lot about starting with the end in mind, meaning be explicit, don’t rely on anecdotal drive-by conversations. Write the concept of operation down in a document so that others can reflect on it as you go through the digital transformation.
A concept of operation is not a technical document. It describes the business:
Too often, digital transformation projects fail because we didn’t start with what success looks like. We simply made the assumption and moved forward, and when things don’t materialize, of course, you wind up with almost 75% failure rate in terms of what, today, we call digital transformations. Overpromises usually wind up with under delivery.
Joel: Scott said, “start with the end in mind and understand what you’re trying to achieve.” Combine that with the ideal principle of “start where you are.” Make sure that you understand your current condition and your current arrangements and what you’re trying to change.
Almost no organization can start with a completely clean slate, but they really need to be very declarative about what they’re trying to achieve. Then dealing with the security elements from the beginning not after the fact, so that they’re not trying to retrofit the choices that you make.
Andrew: Yes, and they talk about when you’re doing these things [it’s important to] build and revisit your security strategy. You’re making major changes and so the threat surface changes constantly as you’re doing your transformation. This is the right time to revisit or rebuild your security strategy to ensure that your control set is present throughout the new environment. And it is also a great opportunity to show how your current security investments are actually helping to secure your new digital lines of business.
How often should you review and consider rebuilding your security strategy?
Joel: In this day and age, I can’t imagine looking at your security strategy less than annually and frankly probably more regularly. There’s the notion that strategy has a very long-enduring horizon. I don’t think that’s very practical considering the level of threat and, therefore, the level of business risk that’s associated with cybersecurity.
Andrew: [Info-Tech also recommends] establishing a vendor security program. Data is moving out of datacenters and onto third-party environments. Without security requirements built into agreements, and clear visibility into vendor security capabilities, that data could be a major source of risk. A robust vendor security program will create assurance early in the process and help reinforce the responsibility of securing data with other parts of the organization.
How often should an organization perform a third-party risk assessment?
Scott: So many of us will look at that same annual benchmark and say at least annually. The auditor wants to see that you’re doing that at least annually. What we say is you need to be assessing your vendors at the pace of business.
The first thing you have to recognize is when you bring a vendor in, and you pass data to the vendor you are transferring risk to that vendor. That vendor becomes part of your continuous staff. But as the business changes, as the evolution of how you use that vendor changes, you need to reassess the risk that you’ve transferred to them.
It could be about not passing as much data. It could be that the vendor has been very successful and now you’re going to pass three times the amount and types of data to that vendor. All of that should be part of a continuous risk assessment to make sure that the risk you’re transferring is explicit, that it’s not based on assumptions, and that you’re validating this is a sensible decision to make with respect to placing the custody of that data with that vendor.
Andrew: We’ve got a lot of key players out there and we need to educate them. These business units are bringing in third parties and we have a transformation that’s happening, but only 16% of security leaders and executives report alignment between security and business processes during digital transformation.
If security is too low a priority, then key players in your transformation efforts are likely unaware of how security risks will impact their own success. It will be incumbent upon the CISO to start that conversation.
What are some ways that you would use to start such conversations to engage and educate stakeholders?
Joel: There’s a temptation to speak in technical terms and firewalls and internal operational metrics and the like. That really doesn’t engage the rest of the business, especially at the C-suite and board level. There needs to be a connection to enterprise risk and the risk to the business with technical foundations, but it needs to be relevant to the other stakeholders. How is this going to affect revenue? What’s the probability of a loss of disruption of operation or brand impairment from the risk of a breach?
In fact, investing in trust elements in improved security and certifications and things that simplify the interactions with customers accelerates revenue. But it takes an investment to get to that level. In our clientele, there are places where the first thing that happens in an engagement is a 300-line questionnaire about security posture, especially if the client is going to hold their customer’s data. And the idea of getting them past that just to talk the risks and the advantages of simplifying and codifying their responses to these questionnaires or through certifications take at least a big chunk of the questions off the table is a big press forward.
So, getting key players to understand how you’re changing the risk profile and customer’s assessments of your risk profile is a really big advantage to the organization – and frankly, it puts the CISO in a much better posture within the organization
Scott: If I can just add to that a quick concept . . . one of the things we work with the leadership teams across our client base, but also folks that we mentor, is the idea of a risk level agreement. Because the business side of the house doesn’t have a security problem they have a risk problem, to Joel’s point. They need to maintain trust and they take on risk, so we set the communication up using a risk level agreement. Here are the risk scenarios, here’s the likelihood and impact of that risk, and here is how much of that risk can be burned down with a practical investment in security controls. Put with the problem in terms of risk and trust to the business and you’re far more likely to get the connection with the stakeholders.
Andrew: All very good points. Now let’s talk about the number two top priority…
Andrew: Obviously, remote work poses unique challenges to cybersecurity teams. The personal home environment may introduce unauthorized people or unknown network vulnerabilities, and the organization loses nearly all power to influence the daily cyber hygiene of its users that are out there remotely.
In addition, the software used for enabling remote work itself can be a target of cybersecurity criminals. [Per StatCan, 2021]:
So, they [Info-Tech] talk about maturing our identity management. Compromised identity is one of the main vectors to breaches in recent years. Stale accounts, contractor accounts, misalignment between HR and IT – the lack of foundational practices leads to headline-making breaches every week. So, tightening up identity control to keep your organization out of the newspaper is pretty important.
How often do you think organizations should review their account identities, roles, and authorizations?
Scott: This is something we wrestle with every day with our clients. The first observation is essentially at the root of what you’ve just been talking about here, and that is that there is no physical perimeter anymore. The perimeter is around the identity and the identities move – whether it’s travel for business or working from home, the identities are constantly on the move. So, we should continuously be revisiting the identities we have – person and non-person entities, but let’s focus on the person entities. We should continually revisit who has access and to what, and do they need it. At a minimum, every time that individual – represented by the identity – whenever they change roles, we should be revisiting the permissions they have.
One of the things we take for granted in most of the environments we work in [is that] we have what we call the discretionary access control approach, meaning if I own that data [then] I determine who I can share it with and who becomes an editor versus a reader, etc. Very often all we think about in terms of providing access is granting privileges. We often never think about, oh, I need to take that back. Joe no longer needs to see that particular briefing, so I need to reduce privileges.
That should be something that we start with training, but also build it into our procedures. It also should take into the account the fact that maybe I should have reduced privileges by default if I’m coming in from my home network. If I’m VPN-ing into the business, maybe that I will still get access into the financial system, but only for read access as opposed to being able to process checks for some huge amount of money. All of that needs to consider not just the identity, but also do we trust the entire path coming into the corporation and the business system the identity is currently using.
Andrew: So, educating users [on security best practices when working remotely] is important. We’re talking about the need to apply settings to configure and secure things on their home network. A lot of times, they’ll install things and just use the default settings. And you’ve got to encourage them to use strong passwords and show them how to identify suspicious emails that might be coming in.
What are some good ways to educate our remote workforce?
Joel: Recognizing that the home network is now an extension of your corporate network. For people who are working from the endpoint, it really means making sure you’re helping them understand what makes them vulnerable at home and, therefore, what makes their own vulnerability a factor in your corporate risk management.
Things like teaching people how to deal with phishing and how to apply strong passwords to their Wi-Fi settings or other parts of the network. And we can do that with training and even gamification to get people engaged.
I think there’s another point where the company has to take specific actions, not just accept the condition of home and personal services as the default for its own environment. That means setting standards for how people work at home and what the expectation is for the controls that are required in their work-from-home configurations.
Andrew: Talking about working from home, you’ve got unknown endpoints, unknown networks, other unknown devices – IoT and other things that might be out there. And the home workstation could be used for non-work purposes. So, it’s important to gain visibility into those endpoints and keep the detection and resolution times short for when there’s something that’s happening that shouldn’t be happening.
What are some ways that you would use to gain visibility or things that you would recommend for those working from home remotely?
Scott: We should start by ensuring that we’ve got some type of endpoint detection and recovery – EDR [endpoint detection and response] capability on the endpoint. Ideally, we’ve got it sending information – instrumented properly – but sending information to a managed platform an MDR [managed detection and response] or an MSSP [managed security service provider]. Ideally we’ve got that because we have no visibility into the platform that’s reliable without that.
Secondarily, we can run some type of user behavior analytics to be able to monitor the user activity. Now let me be clear, this isn’t to look for malicious activity but it’s to profile what is expected activity. So what is normal for that particular user such that when we see activity on the machine that’s highly exceptional we get a flag to say, “wait a second, Scott doesn’t usually delete or encrypt all these files in the 2:00 AM hour.” That would help significantly to be able to instrument that endpoint. A
And lastly, one of the things we talk about all the time is split tunneling to try to disable it first and foremost. But realistically, a lot of people still print . . . especially in the home environment . . . to try to use that as an exception. If somebody shouldn’t be in an always-on VPN kind of a mode, but if we allow split tunneling and allow them to drop off, that should be a process that’s documented and audited. So first they make the request. It’s approved or processed, and the audit trail records the fact that Scott dropped off or split the tunnel in order to print, but then came back after he did that. All of that improves the visibility of that endpoint when it’s outside of our control perimeter.
Andrew: Ease of use is another area to consider. Many workers complain that the corporate technology solution makes it difficult to get their work done. Employees will take productivity over security if we force them to make a choice, so IT needs to listen to end users’ needs and provide a solution that is nimble and secure.
I came up with this thing called the “KISS rule.” No, it’s not “keep it simple stupid.” It’s “keep information security simple.”
What sort of things have you seen employees do and what would you recommend they do?
Joel: It comes in many forms. Adding software that they find useful even if it’s not approved software or circumventing the vendor risk assessment process. Using personal devices and moving information that shouldn’t be moved to those devices in ways that make it really hard to track where information has gone.
They’ve added secure devices that corporate IT won’t know about in their home networks. People have their own ecosystems at home now – Apple TV or [Amazon] Fire TV and home automation IoT devices that are being controlled and maybe being controlled with credentials that are shared with their corporate-provisioned devices.
We have an example of an executive sharing his Apple ID with his entire family, so suddenly content that was intended to be contained was shared across all of his home devices and family members.
So, make sure that you understand that for mixed-use devices you still need to take care about what the rules ought to be and there ought to be guidance from corporate IP and IP security about effective practices to ensure that you don’t have accidental paths.
The point about choosing functionality and ease of use is always going to be there. People are going to try to find ways to make things easier to do. Corporate IT and cybersecurity teams need to understand the use patterns in ways that they can enable them and still add the necessary controls to make them less scary.
Fletcher Previn, who’s the CIO at Cisco now and was the CIO at IBM, famously said in one of his standard presentations, “Why does it feel like the Jetsons at home and the Flintstones at work?”
Because the environments are so much more locked down and feel so much less capable, how do you find that balance in those environments that allow you to have a really good user experience and still have controls in place and not just put it on the end user to figure it out. So, we have to look beyond the physical boundaries or the corporate boundaries and look at the use patterns that are most affected.
Andrew: Now I’m going to touch on topic that is pretty important here. We’re talking security and, honestly, everything is getting more complex day after day. But they say the number one priority for 2022 the number one priority is…
Let’s talk about providing career development opportunities to help those that are currently working for your organization – to educate them.
Many security professionals are dissatisfied with their unclear career development paths. To improve retention, organizations should provide their staff with opportunities and clear paths for career and skills advancement.
What are some good ways to steer security professional career pathways?
Scott: We often hear clients say, “We’ve got all this open headcount and we want to hire the best.” Our response is typically, “Everyone wants to hire the best.” You should be the company that’s known for developing the best. You want to be that company whose brand is on someone’s resume, and someone says, “You did security for XYZ? You’re definitely going to be fantastic for us – we know they develop the best talent.”
So, start with putting a program together that builds to that objective. That provides career paths and does so in both a practical and consumable way. Things like internal internships. Often we’ll work with an organization that has an internal helpdesk and we’ll say, “Let’s rotate the helpdesk through the security operation center and allow them to do Tier 1 work. And let’s train them on doing the basics of modern detection or even pull them into cyber threat intelligence and train them on what CTI [cyber threat intelligence] is and how we leverage CTI to focus our hunts – automated and manual.
Deliberately build a program that acknowledges it isn’t just about sending them to a class or getting them through a certification. All of that is useful but they need to be paired with other professionals, and those professionals need to have the time to mentor new and developing staff. If it’s not built-in as a key objective for them and if it’s not something that they can partition time every week to make sure they’re making the investment in that next generation, let’s face it, it isn’t going to happen.
Andrew: Facilitating a work-life balance is important as well, right? Many security professionals say that they experience that burnout. So, promoting work-life balance within your organization will help retain critical skills as well.
What are some good ways you know for security professionals to maintain a good work-life balance?
Joel: I wish there was a silver bullet on this one. This one is really hard. And working from home doesn’t improve it much because the boundaries of work and non-work have largely evaporated.
The challenge is that most cybersecurity organizations are understaffed and they’re in a war for talent. There was a recent infographic published by NIST’s national initiative for cybersecurity education that put some statistics on the table. One very telling one from Cybersec is that there’s about 2.5 million unfilled jobs but the number of openings in the U.S. is about 600,000 of the jobs. So, it’s an indication that organizations feel understaffed and, therefore, are stretching to make do with who they have. They’re afraid to lose them but they’re also afraid not to get the job done, so there’s a natural cycle of stress that comes from that.
As we said earlier, the threats are only getting more severe so finding ways to give people breaks . . . give people the ability to take on mentees who can then help them has a net benefit. Investing in cybersecurity knowledge early in people’s careers so that they’re able to contribute on this front, so it’s not just a couple of experts who are trying to handle all of the spinning plates at the same time.
Andrew: Another recommendation is to be open-minded when hiring. To broaden the candidate pool, organizations should be open-minded when considering who to hire.
Finding somebody who’s trainable that has the personality and the natural talents to be in a cybersecurity position is important.
What are some good ways you have used to find needed talent?
Scott: It’s going to depend upon the seniority of the job that I’m trying to fill. If it’s a very senior job then I will be participating in conferences, for example, roundtables, birds of the feather networking, whether it’s within the community with the different associations or outside the community just on LinkedIn. For senior talent, I’m absolutely looking for the years that they’ve had and in some cases certifications – not that it attests to the quality of their work but [it shows] that they’ve got some base-level knowledge.
If I move downstream though to the more junior people, it always fascinates me to read these posts where [employers] are looking for an entry-level position and they’ve got three certifications required. And if you pull back on the certification you realize anybody that has achieved the certification has 15 years of experience. By definition, he or she is not going to be interested in an entry-level position.
But I’ll tell you there’s one thing that I look for in the entry-level position, which I think is fundamental to success in our industry, and that is curiosity. I have hired and worked with professionals from physicists, economists, archaeologists – people that if you just looked at their education and their early career, you would never guess there’d be an affinity let alone a skill in our particular industry.
I’m finding the one thing that’s coming across all of them isn’t necessarily even their technical taproot, but it’s their curiosity. They want to dive in and learn – continuously learn – which is important because the space we’re in every day is different. The threat evolves and technology evolves. That curiosity is what pulls them into it and breeds their success. If you don’t have the curiosity, I’m afraid you just can’t build it. It’s not something we can give to our staff if they don’t come in the door with it.
Andrew: It’s also about being inclusive. Hire a diverse team and create an inclusive environment where they can thrive.
What kind of incentives have you used in the past to drive diversity?
Joel: This is an area that takes constant vigilance. Make sure you’re casting a very wide net. Don’t just go back to the same source all the time for candidates. And for the people that you promote, make sure that you’re being inclusive in the candidate pool and authentically inclusive in the participation across the organization. To the previous point about keeping an open mind, look for different mixes of talent from different backgrounds and sources and you’ll get a more effective team.
And that’s what you’ll get with Zones. We offer end-to-end professional and managed services for vulnerability assessments, managed security operations, access policies, and information security governance.